Hierarchical Network Design Overview
You can use the hierarchical model to
design a modular topology using scalable "building blocks" that allow
the network to meet evolving business needs. The modular design makes the
network easy to scale, understand, and troubleshoot by promoting deterministic
traffic patterns.
Cisco introduced the hierarchical design
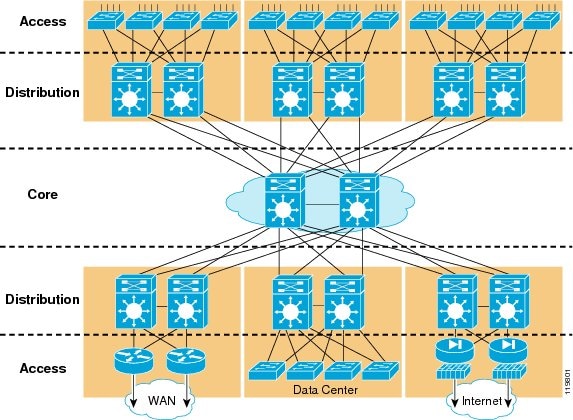
model, which uses a layered approach to network design in 1999 (see Figure 1).
The building block components are the access layer, the distribution layer, and
the core (backbone) layer. The principal advantages of this model are its
hierarchical structure and its modularity.
Figure 1 Hierarchical Campus Network Design:
In a hierarchical design, the capacity, features, and
functionality of a specific device are optimized for its position in the
network and the role that it plays. This promotes scalability and stability.
The number of flows and their associated bandwidth requirements increase as
they traverse points of aggregation and move up the hierarchy from access to
distribution to core. Functions are distributed at each layer. A hierarchical
design avoids the need for a fully-meshed network in which all network nodes
are interconnected.
The building blocks of modular networks
are easy to replicate, redesign, and expand. There should be no need to
redesign the whole network each time a module is added or removed. Distinct
building blocks can be put in-service and taken out-of-service without
impacting the rest of the network. This capability facilitates troubleshooting,
problem isolation, and network management.
Core Layer
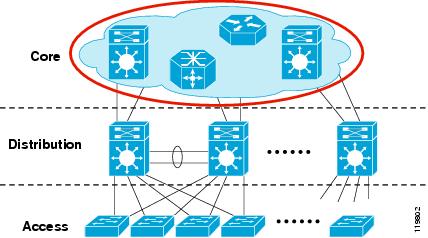
In a typical hierarchical model, the
individual building blocks are interconnected using a core layer. The core
serves as the backbone for the network, as shown in Figure 2.
The core needs to be fast and extremely resilient because every building block
depends on it for connectivity. Current hardware accelerated systems have the
potential to deliver complex services at wire speed. However, in the core of
the network a "less is more" approach should be taken. A minimal
configuration in the core reduces configuration complexity limiting the
possibility for operational error.
Figure 2
Core Layer:
Although it is possible to achieve redundancy with a
fully-meshed or highly-meshed topology, that type of design does not provide
consistent convergence if a link or node fails. Also, peering and adjacency
issues exist with a fully-meshed design, making routing complex to configure
and difficult to scale. In addition, the high port count adds unnecessary cost
and increases complexity as the network grows or changes. The following are
some of the other key design issues to keep in mind:
•Design the core layer as a high-speed, Layer
3 (L3) switching environment utilizing only hardware-accelerated services.
Layer 3 core designs are superior to Layer 2 and other alternatives because
they provide:
•Use redundant point-to-point L3
interconnections in the core (triangles, not squares) wherever possible,
because this design yields the fastest and most deterministic convergence
results.
•Avoid L2 loops and the complexity of L2
redundancy, such as Spanning Tree Protocol (STP) and indirect failure detection
for L3 building block peers.
Distribution Layer
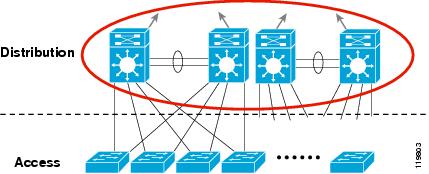
The distribution layer aggregates nodes
from the access layer, protecting the core from high-density peering (see Figure 3).
Additionally, the distribution layer creates a fault boundary providing a
logical isolation point in the event of a failure originating in the access
layer. Typically deployed as a pair of L3 switches, the distribution layer uses
L3 switching for its connectivity to the core of the network and L2 services for
its connectivity to the access layer. Load balancing, Quality of Service (QoS),
and ease of provisioning are key considerations for the distribution layer.
Figure 3
Distribution Layer:
High availability in the distribution layer is provided
through dual equal-cost paths from the distribution layer to the core and from
the access layer to the distribution layer (see Figure 4).
This results in fast, deterministic convergence in the event of a link or node
failure. When redundant paths are present, failover depends primarily on
hardware link failure detection instead of timer-based software failure
detection. Convergence based on these functions, which are implemented in
hardware, is the most deterministic.
L3 equal-cost load sharing allows both uplinks from the core
to the distribution layer to be utilized. The distribution layer provides
default gateway redundancy using the Gateway Load Balancing Protocol (GLBP),
Hot Standby Router Protocol (HSRP), or Virtual Router Redundancy Protocol(VRRP).
This allows for the failure or removal of one of the distribution nodes without
affecting end point connectivity to the default gateway.
You can achieve load balancing on the
uplinks from the access layer to the distribution layer in many ways, but the
easiest way is to use GLBP. GLBP provides HSRP-like redundancy and failure
protection. It also allows for round robin distribution of default gateways to
access layer devices, so the end points can send traffic to one of the two
distribution nodes.
Access Layer
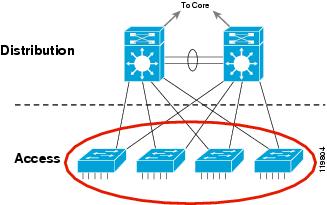
The access layer is the first point of
entry into the network for edge devices, end stations, and IP phones (see Figure 5).
The switches in the access layer are connected to two separate distribution
layer switches for redundancy. If the connection between the distribution layer
switches is an L3 connection, then there are no loops and all uplinks actively
forward traffic.
Figure 5
Access Layer:
A robust access layer provides the following key features:
•Inline power (POE) for IP telephony and
wireless access points, allowing customers to converge voice onto their data
network and providing roaming WLAN access for users.
The hardware and software attributes of
the access layer that support high availability include the following:
•System-level redundancy using redundant
supervisor engines and redundant power supplies. This provides
high-availability for critical user groups.
•Default gateway redundancy using dual
connections to redundant systems (distribution layer switches) that use GLBP,
HSRP, or VRRP. This provides fast failover from one switch to the backup switch
at the distribution layer.
•Operating system high-availability features,
such as Link Aggregation (EtherChannel or 802.3ad), which provide higher
effective bandwidth while reducing complexity.
•Prioritization of mission-critical network
traffic using QoS. This provides traffic classification and queuing as close to
the ingress of the network as possible.
•Security services for additional security
against unauthorized access to the network through the use of tools such as
802.1x, port security, DHCP snooping, Dynamic ARP Inspection, and IP Source
Guard.
•Efficient network and bandwidth management
using software features such as Internet Group Membership Protocol (IGMP)
snooping. IGMP snooping helps control multicast packet flooding for multicast
applications.
For more information:
Cisco Enterprise
Service Provider Function Area
High availability network services


No comments:
Post a Comment