Cisco SAFE Architecture
Cisco SAFE Architecture
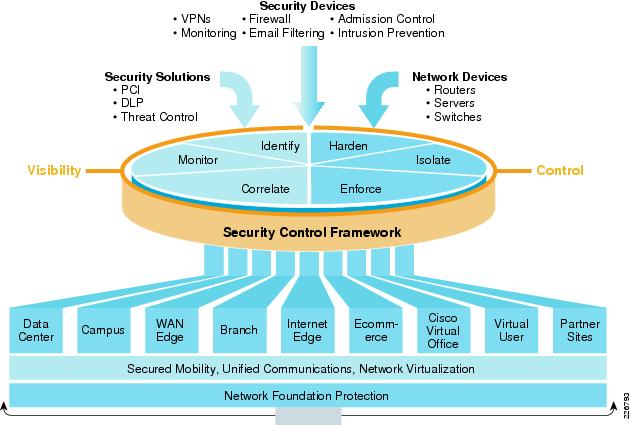
Total Visibility and Complete Control are two of main
components of SCF (Security Control Framework). Network security is a function
of visibility and control. Without visibility, there is a lack of control, and
without control, you are missing key elements of security. The success of a
security policy depends on solid visibility and control. Within SCF, there are 6
security actions used to enforce security policy and allow for visibility and
control. Visibility is improved with identify, monitor, and correlate security
actions; and control is enhanced through the harden, isolate, and enforce
security actions. Each of these security actions is further defined in the SCF
model.
Trust and Identity Technologies:
ACL
Firewall
Cisco Network Admission Control (NAC) Appliance
802.1X
Cisco Identity-Based Network Services (IBNS)
802.1X and EAPoL
Detecting and Mitigating Threats
Endpoint protection
Application security and content security defense
Infection containment
Inline IPS and anomaly detection
Threat Detection and Mitigation Technologies
Here are some examples of Cisco threat-detection and threat-mitigation
technologies:
- FWSM:
Catalyst 6500 Firewall Services Module
- ASA: Adaptive Security Appliance (Robust firewall or NIPS)
- IOS
firewall: Cisco IOS software feature set
- IPS
sensor appliance: NIPS
- IPS:
Intrusion prevention system (IOS feature)
- NAC:
Cisco NAC Appliance
- Cisco
Traffic Anomaly Detector Module: Detects high-speed DoS attacks
- Cisco
IronPort Web Security Appliance (Cisco WSA)
- Cisco
IronPort Email Security Appliance (Cisco ESA)
- Network
management protocols and solutions
- NetFlow:
Stats on packets flowing through router (IOS feature)
- Syslog:
Logging data (IOS feature)
- SNMP:
Simple Network Management Protocol (IOS feature)
- Cisco MARS: Monitoring, Analysis, and Response System
- Remote Monitor (RMON) events
- CPU
and interface statistic
- Cisco
Security Manager
- Cisco NAC Manager
Threat Detection and Mitigation
Security Management Applications
Security Platform Solutions:
Cisco has a variety of security management products and
technologies that allow scalable administration and enforcement of security
policy for the Cisco SCF architecture. These solutions reduce the operational
management and automate many of the common tasks, including configuration, analysis,
incident response, and reporting. Security management platforms include the
following:
- Cisco
Security Manager (CSM) is an integrated solution for GUI configuration management
of firewall, VPN, and IPS policies on Cisco security appliances, firewalls,
routers, and switch modules. CSM has capabilities for security policies to
be deployed by device, by group, or globally for all devices.
- Cisco
Secure Access Control Server (ACS) provides centralized control for
administrative access to Cisco devices and security applications. ACS
provides for AAA security services and supports routers, switches, VPN
services, ASAs, and Cisco NAC clients. In addition, Cisco ACS also
supports back-end directory integration with Lightweight Directory Access
Protocol (LDAP) and Microsoft Active Directory (AD) for authentication
services.
- Cisco
Security Monitoring, Analysis, and Response System (Cisco Security MARS) tor,
identify, isolate, and respond to security threats. MARS understands the
network topology and device configurations from routers, switches, firewalls,
and IPS devices. MARS also can model packet flows on the network.
- Cisco
NAC Manager is an appliance that manages the Cisco NAC servers. NAC Manager
has a web-based interface for managing security policies and online users
that are part of the NAC infrastructure. Cisco NAC Manager acts as an
authentication proxy using Cisco ACS or Microsoft AD.
- System
Administration Host provides a centralized host used to stage
configuration, software images, and implement network changes.
- Network
Time Protocol (NTP) server provides time synchronization to NTP clients such
as routers and switches. Time synchronization is crucial in the analysis
of event correlations.
- Configuration and Software Archive Host serves as a repository to backup device configurations and software images.
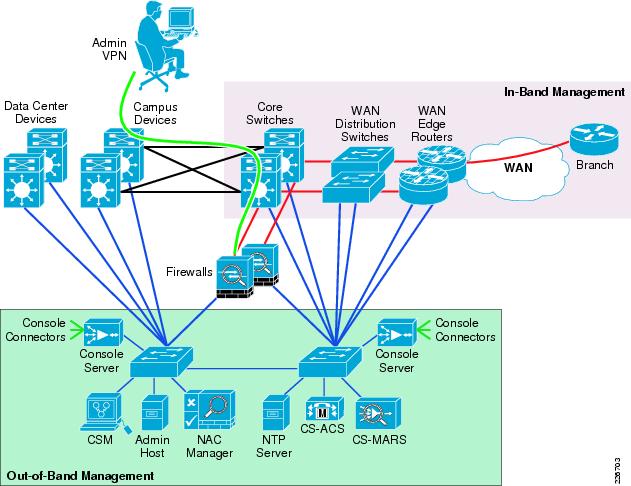
SAFE Management Network: In-Band and Out-of-Band
Integrated Security for Cisco IOS
Cisco IOS Integrated
|
Security Description
|
Cisco IOS firewall
|
Stateful multiservice application-based filtering
|
Cisco IOS IPS
|
Cisco IOS IPS Inline deep packet inspection
|
Cisco IOS IPsec
|
Data encryption at the packet level
|
Cisco IOS Trust and Identity
|
AAA, PKI, SSH, SSL
|
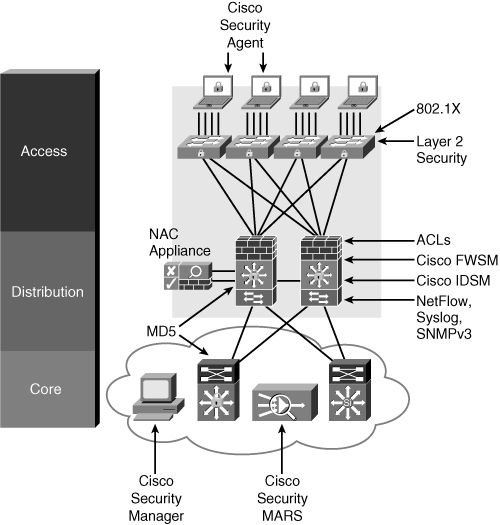
Implementing Security in the Campus
Cisco Security
Category
|
Security Solutions
|
Identity and access control
|
802.1X, NAC, ACLs, and firewalls
|
Threat detection and mitigation
|
NetFlow, syslog, SNMP, RMON, CS-MARS, and NIPS
|
Infrastructure protection
|
AAA, TACACS, RADIUS, SSH, NMPv3, IGP/EGP MD5, and Layer 2
security features
|
Security management
|
CSM, CS-MARS, and ACS
|
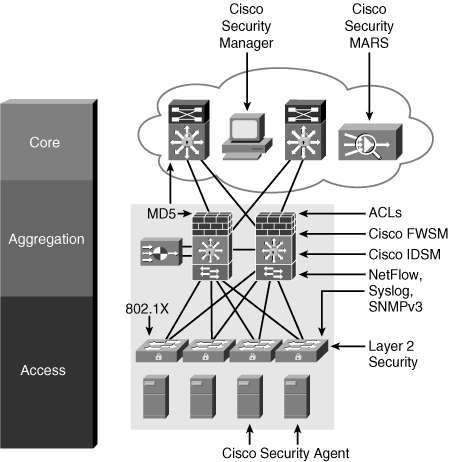
Security in the Data
Center
Cisco Security
Category
|
Security Solutions
|
Identity and access control
|
802.1X, ACLs, and firewalls (FWSM
|
Threat detection and mitigation
|
NetFlow, syslog, SNMP, RMON, CS-MARS, and NIPS
|
Infrastructure protection
|
AAA, TACACS, RADIUS, SSH, SNMPv3, IGP/EGP MD5, and
Layer 2 security features
|
Security management
|
CSM, CS-MARS, and ACS
|
Security in the Enterprise
Cisco Security
Category
|
Security Solutions
|
Identity and access control
|
Firewalls, IPsec, SSL VPN, and ACLs
|
Threat detection and mitigation
|
NetFlow, syslog, SNMP, RMON, IDS modules, CS-MARS, and NIPS
|
Infrastructure protection
|
AAA, CoPP, TACACS, RADIUS, SSH, SNMP v3, IGP/EGP MD5, RFC 2827
ingress filtering and Layer 2 security features
|
Security management
|
CSM, CS-MARS, and ACS
|

I wanted to thank you for this excellent read!! I definitely loved every little bit of it.Cheers for the info!!!! & This is the perfect blog for anyone who wants to know about this topic.
ReplyDeletemachine to machine
I just wanted to let you know that you've inspired me to read this post.......Thank you for sharing such a knowledgeable information..:)
ReplyDeletem2m